About 14,703 results found.
(Query 0.00600 seconds)
- All
- Images
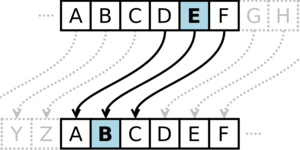
Die Caesar-Chiffre ist eine recht einfache Methode zum Verschlüsseln - aber es ist auch leicht, die Verschlüsselung zu knacken.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
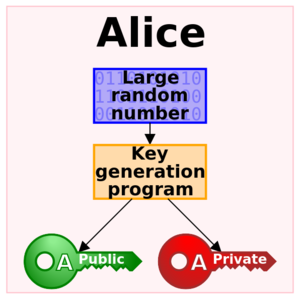
Die asymmetrische Verschlüsselung mit öffentlichem Schlüssel wird bei modernen E-Mails für den sicheren Austausch von Nachrichten verwendet.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
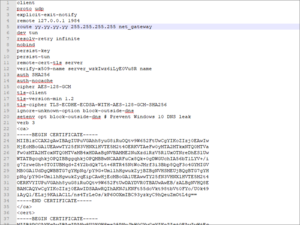
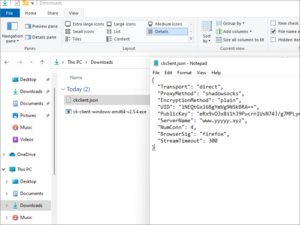
OpenVPN client configuration for Cloak
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion
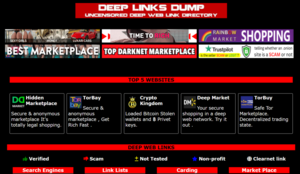
screenshot of DeepLinksDump darkweb market
wikiiinwxf6xeb5mhiztmwxvf3mv7spijedoba6fjx7bjm4tggggipad.onion

illustration of a free speech cat talking on a megaphone
annualreport.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
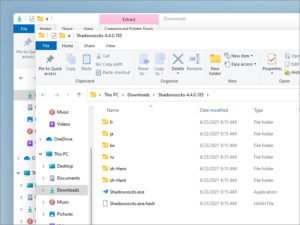
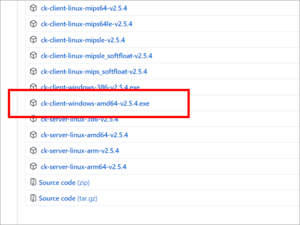
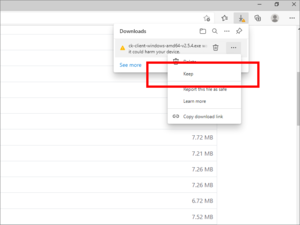
Extract Shadowsocks client for Windows
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

Download Shadowsocks client for Windows from GitHub
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion