About 13,403 results found.
(Query 0.01100 seconds)
- All
- Images

Methamphetamine hydrochloride synthesis via Leuckart amination
mumxbkms57zlmezjvdjj63cffd2fgzsvjv3sc5muzeptqyx5er7bxqqd.onion

Tor Browser Downloader (Whonix) Download Confirmation
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion
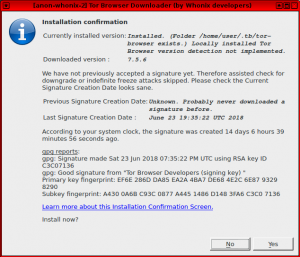
torbrowser-updater_signature_verification_screen.
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion

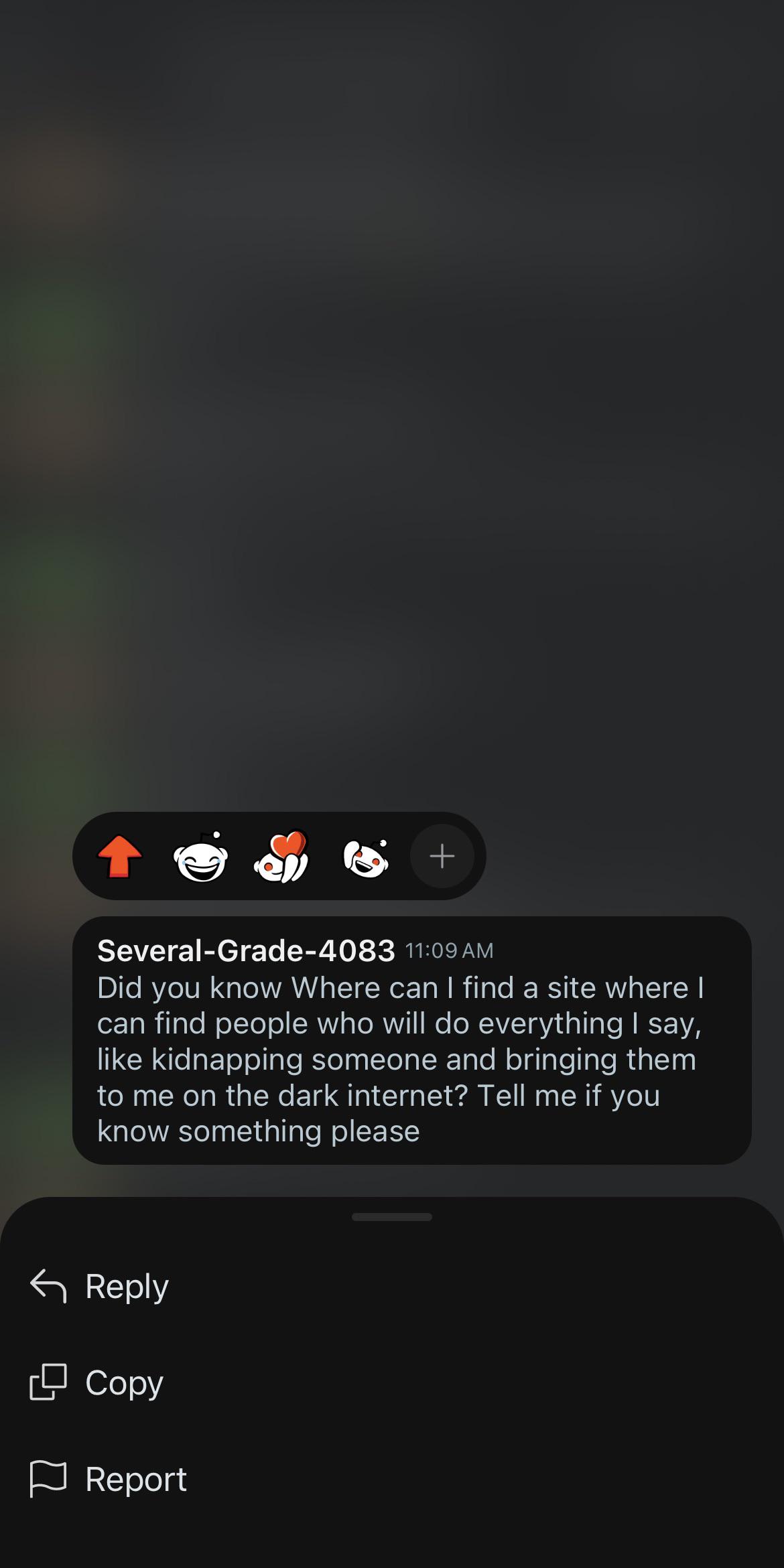
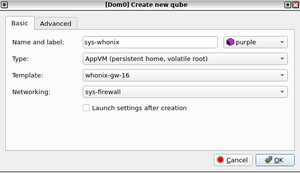
Displaying Tor circuit information in Tor Browser
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

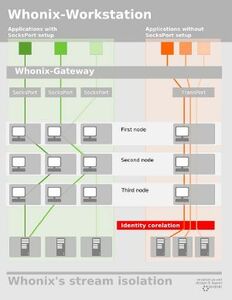
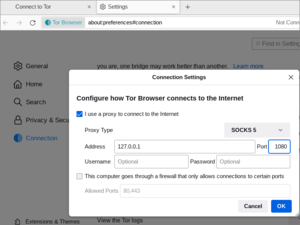
Tor Browser connecting to the Tor network
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion