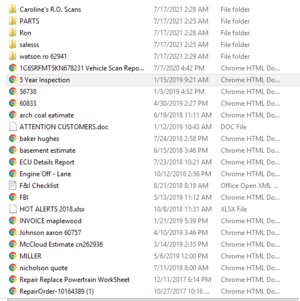
About 37,864 results found.
(Query 0.01000 seconds)
- All
- Images

Phantom Hackers Hire Hackers – Hackers For Hire – Hire a Hacker Online
phantoquu6dx3popx6vrvi5ngsoglhbsi6mzdqgg5niuth366gvxlzid.onion

A person places a gold Bitcoin coin into a wallet, ready to buy crypto on Coinmama.
coinmamailtcrg7fw6uorut3d35bk35rtmntkrtb4fgeov6pefvfutqd.onion

When you copy your onion service to Tor browser, you will see the Laravel PHP Framework landing page. You will need to refresh your Tor browser several times to see the landing page.
dwebkjkovsjobzrb45dz6prnlifnapiyp2dba33vcmcsaikr2re4d5qd.onion

How to get a small business email address with Tuta Mail
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Hire a private Investigator Online , Hire a Detective Online , Hire hitman Online, hire a private investigator to find someone, hire a private investigator for cheating spouse
py45pjcu3uzum4jva2xrkjkjqgvwqfbe47azvzeghanyatqch65ao3yd.onion
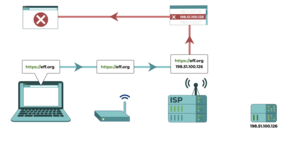
In this diagram, the Internet Service Provider cross-checks the requested IP address against a list of blocked IP addresses. It determines that the IP address for iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion matches that of a blocked IP
ssd.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
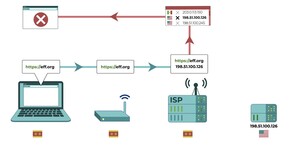
A computer attempts to connect to iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion’s US-based IP address. At the Internet Service Provider’s level, the request is checked: the IP address for iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy4
ssd.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

The angular outline of three faces as a computer might see them, colored like a rainbow
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Hire a Hacker to Catch a Cheating Husband
forum4mfz4tg62angjcgdt5n6ymbpizizdg3g3gsp5t4krtevnnabvqd.onion

Hire a Hacker to Catch a Cheating Husband
forum4mfz4tg62angjcgdt5n6ymbpizizdg3g3gsp5t4krtevnnabvqd.onion
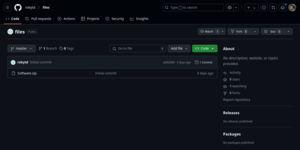
A GitHub repository containing a single file - "Software.zip" - which as we all know is the best way to use git.
tweedge32j4ib2hrj57l676twj2rwedkkkbr57xcz5z73vpkolws6vid.onion

Shadowsocks client systemd service file
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

Hire a Hacker for any hacking service
lionznqcaixgvjnpn6yih6phu2xk2mc6nsouupv6tf2hf5h7yzbud4qd.onion

FACEBOOK & INSTAGRAM HACKING SERVICE
pbaqnj5mrr2fw3z2bevwihge62zvvkhz4mwfmdnfezzgd2l2e4qbbmad.onion

In this diagram, the computer uses a VPN, which encrypts its traffic and connects to iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion. The network router and Internet Service Provider might see that the computer is using a VPN, but the data
ssd.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Hire a Hacker for Tracing down an IP Address
latest2fombxgqmvju47iexyqql4wnnrakwqi4n4bi3gksyjk7afuvqd.onion
investigatore privato Roma, investigatore privato milano , investigatore privato napoli, investigatore privato vicino a me, investigatore privato torino
py45pjcu3uzum4jva2xrkjkjqgvwqfbe47azvzeghanyatqch65ao3yd.onion

The angular outline of three faces as a computer might see them, colored like a rainbow
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion