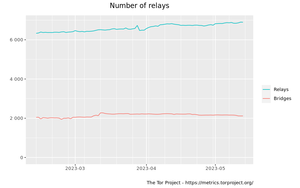
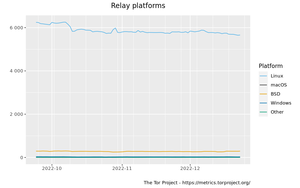
About 13,403 results found.
(Query 0.00700 seconds)
- All
- Images

../_images/duck_duck_go_hidden_service.png
mf34jlghauz5pxjcmdymdqbe5pva4v24logeys446tdrgd5lpsrocmqd.onion

Bandwidth spent on answering directory requests graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion
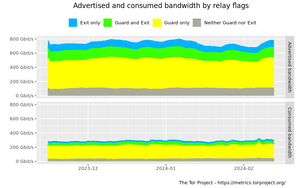
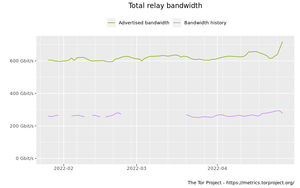
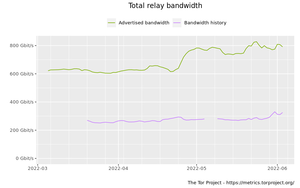
Advertised and consumed bandwidth by relay flags graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion

Bandwidth spent on answering directory requests graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion
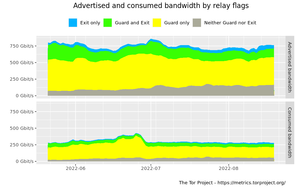
Advertised and consumed bandwidth by relay flags graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion

Proton VPN Anonymously and Free without paying !
lionznqcaixgvjnpn6yih6phu2xk2mc6nsouupv6tf2hf5h7yzbud4qd.onion
BridgeDB requests by distributor graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion
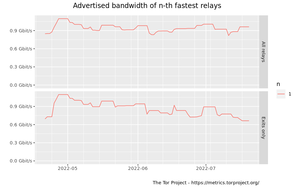
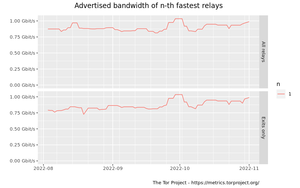
Advertised bandwidth of n-th fastest relays graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion
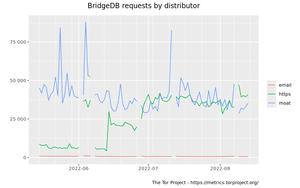
BridgeDB requests by distributor graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion
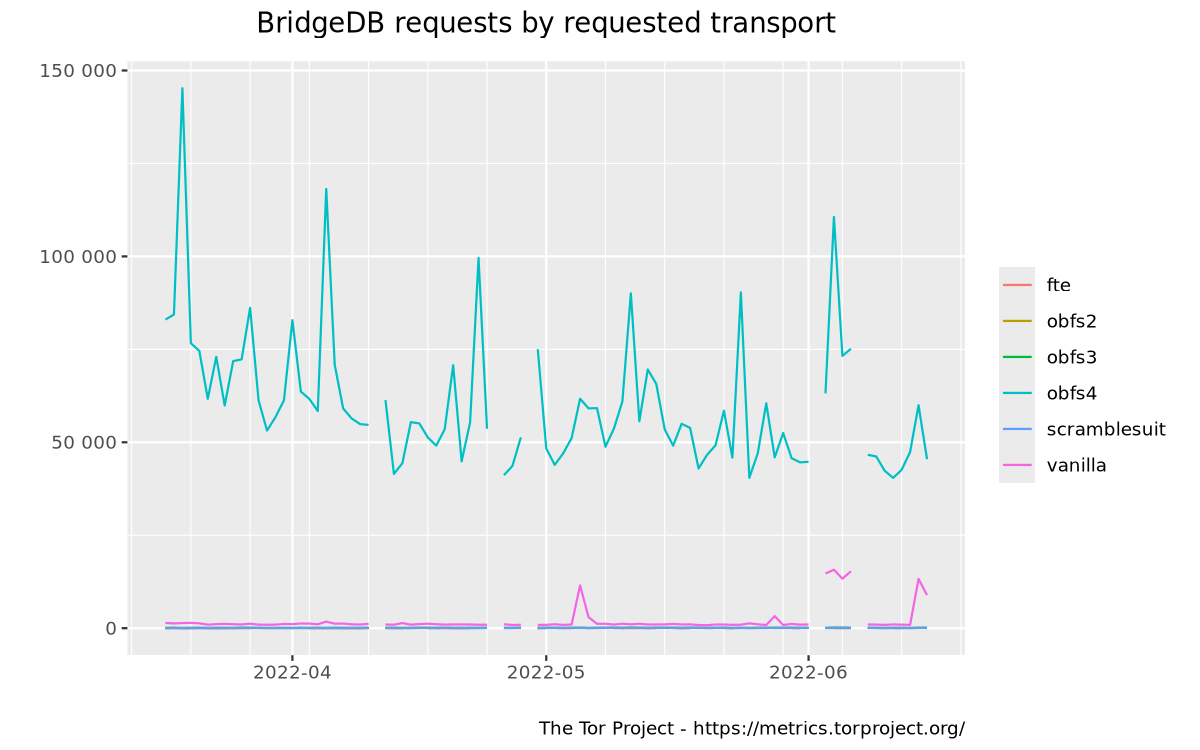
BridgeDB requests by requested transport graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion
Advertised bandwidth of n-th fastest relays graph
hctxrvjzfpvmzh2jllqhgvvkoepxb4kfzdjm6h7egcwlumggtktiftid.onion