About 19,691 results found.
(Query 0.05500 seconds)
- All
- Images

Automatic File Translation Software - no traces
lionznqcaixgvjnpn6yih6phu2xk2mc6nsouupv6tf2hf5h7yzbud4qd.onion

Avast Internet Security 2018 - Free until 2038
lionznqcaixgvjnpn6yih6phu2xk2mc6nsouupv6tf2hf5h7yzbud4qd.onion

WX onion shield logo. Created with AI (Flux Schnell)
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion

Whonix silhouette logo. Created with AI (Flux Schnell)
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion

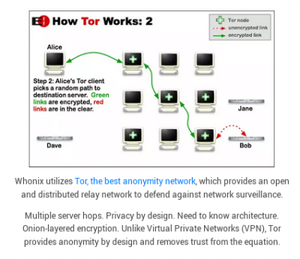
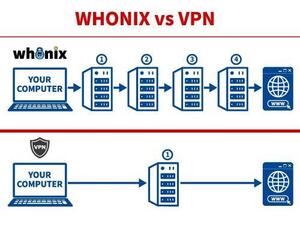
WhonixWhonix vs VPN Logos On The Left
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion

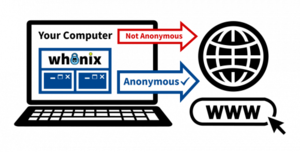
Whonix Connection Without Vanguard Logo
dds6qkxpeiqvogt4y2fd7vtsxq6pvokekb2h4la7jd4iwl4ljuawu5qd.onion