About 25,673 results found.
(Query 0.02400 seconds)
- All
- Images

Sie können Ihr gelöschtes Outlook- oder Hotmail-Konto wieder reaktivieren.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

How to close your Outlook or Hotmail email account.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
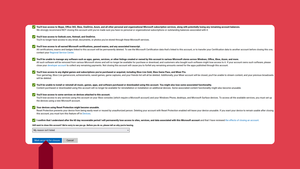
Checkliste, um zu bestätigen, dass Sie verstehen, was das Löschen Ihres Outlook-Kontos bewirkt.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
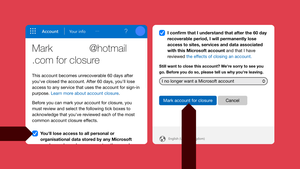
Schritte zum Löschen Ihres Outlook-Kontos auf einem iPhone
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Screenshot der Tuta-Website: Sicher, grün und werbefrei.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Das Tutanota-Logo hat sich von einem Weg zur Privatsphäre zu einem Schalter entwickelt, mit dem man die Privatsphäre auf einfache Weise einschalten kann.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
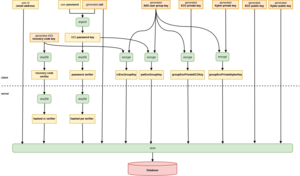
Eine Visualisierung des Umgangs mit Passwörtern und Verschlüsselungscodes.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Basics in Cryptography: What is a password hash?
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Risks of Hiring a Dark Web Hacker: What to Be Aware Of
apqcqk4gowcm2lgltggrouxjwvmatzlwumyvir25ptzuzltyb5u5c2yd.onion

Ethical Considerations of Hacking Messaging Apps: A Deep Dive
apqcqk4gowcm2lgltggrouxjwvmatzlwumyvir25ptzuzltyb5u5c2yd.onion

Hacking Techniques: How a Hacker Exploit Vulnerabilities
apqcqk4gowcm2lgltggrouxjwvmatzlwumyvir25ptzuzltyb5u5c2yd.onion
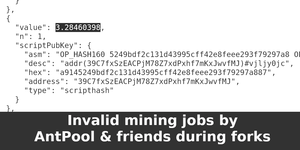
Image for Invalid mining jobs by AntPool & friends during forks
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
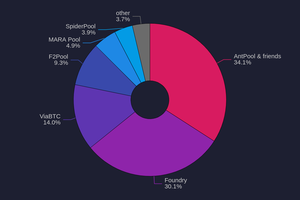
Image for Bitcoin Mining Centralization in 2025
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
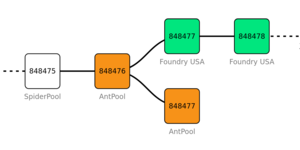
Image for Mining Pool Behavior during Forks
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
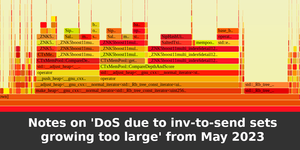
Image for Notes on 'DoS due to inv-to-send sets growing too large' from May 2023
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
Image for peer-observer: A tool and infrastructure for monitoring the Bitcoin P2P network for attacks and anomalies
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for mempool.observer (2019 version)
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Bitcoin Transaction Monitor
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for transactionfee.info (2020 version)
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Timeline: Historical events in the development of Bitcoin
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Contribution: Colab version of the Optech Schnorr / Taproot Workshop
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for GitHub Metadata Backup and Mirror
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for transactionfee.info (2018 version)
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Contribution: Bitcoin Core Project
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Monitoring Taproot Activation
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for miningpool-observer: Observing Bitcoin Mining Pools
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
Image for Update on LinkingLion: Reduced activity and a statement by LionLink Networks
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Invalid F2Pool blocks 783426 and 784121 (April 2023)
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
Image for Invalid MARAPool block 809478
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Six OFAC-sanctioned transactions missing
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
Image for Vulnerability Disclosure: Wasting ViaBTC's 60 EH/s hashrate by sending a P2P message
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Block Template Similarities between Mining Pools
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Workshop: Writing a NixOS module for YOUR_APP
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for An overview of recent non-standard Bitcoin transactions
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for CPU usage of Bitcoin Core peers
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Advancing Bitcoin Workshop: Tracing Bitcoin Core v23.0
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
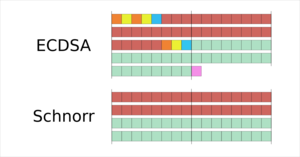
Image for Evolution of the signature size in Bitcoin
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Following the Blockchain.com feerate recommendations
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
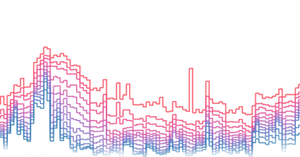
Image for Plotting the Bitcoin Feerate Distribution
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Frequently Asked Questions: Bitcoin Transaction Monitor
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
Image for The Incomplete History of Bitcoin Development
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
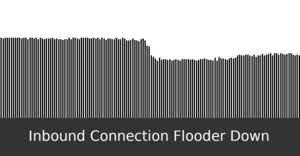
Image for Inbound Connection Flooder Down (LinkingLion)
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for A List of Public Bitcoin Feerate Estimation APIs
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for The stair-pattern in time-locked Bitcoin transactions
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Extracting the Private Key from Schnorr Signatures that reuse a Nonce
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
Image for The daily BitMEX broadcast at 13:08 UTC
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for On anyone-can-spend Pay-to-Taproot outputs before activation
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for Updates on USDT in Bitcoin Core
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion
Image for P2TR spending transactions missing from F2Pool and AntPool blocks (2021)
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for 2022 Review and 2023 Outlook
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion

Image for LinkingLion: An entity linking Bitcoin transactions to IPs?
kd6oox7aowzt5ypwdp2o5curwkgtjjzzk33ecejomm52epjr74daoeid.onion