About 4,030 results found.
(Query 0.01100 seconds)
- All
- Images
Screenshot der Tuta-Website: Sicher, grün und werbefrei.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Das Tutanota-Logo hat sich von einem Weg zur Privatsphäre zu einem Schalter entwickelt, mit dem man die Privatsphäre auf einfache Weise einschalten kann.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Illustration of a woman holding up a magnifying glass to different applications on a computer screen. In front of the left side of the computer screen is a dark red shield with the Tuta logo.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

woman with pink hair and glasses smiling at the camera
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

An envelope with a pained face. Its envelope has been ripped open, exposing the message.
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
Komposition des Tuta-Kalenders in seinem neuen Look auf Desktop, iPad und iPhone.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

h-b-horn-bolgesi-anarsistleri-tigray-soykirimina-k-1.png
anarsizmhxyuq7nfuw2hirvflh2ly2p3ddczsnmxmbsn73rgiyytpyqd.onion
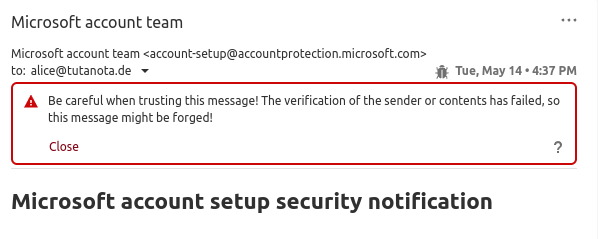
Das Bild zeigt eine gefälschte E-Mail-Warnung im Tuta-Mail-Client.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Authentication Failed - this warning is shown when DKIM checks fail for an email.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Australia could be the first of the 5 Eyes to abolish end-to-end encryption - will others follow?
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Ein Beispiel dafür, wie Tuta die Zero-Knowledge-Architektur in unserer Kontaktfunktion eingeführt hat
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Man checking infrastructure equipment.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Ein Beispiel dafür, wie Tuta Mail alle Daten im Mail-Client vor dem Versand verschlüsselt.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Screenshots of Organic Maps mobile app.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
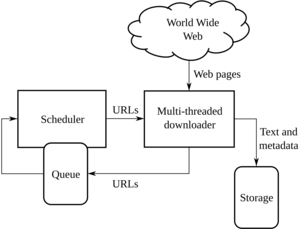
Wie Webcrawler arbeiten, um Suchindizes zu erstellen.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
OpenStreetMap is the backbone of the best alternatives to Google Maps.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Google has equipped cars and people for photographing the world.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
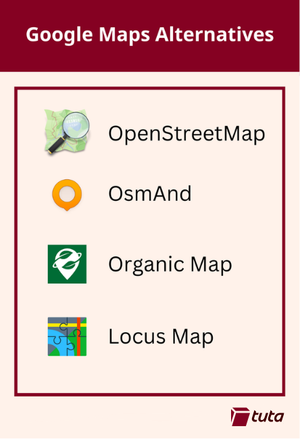
Our recommendations for an alternative to Google Maps
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
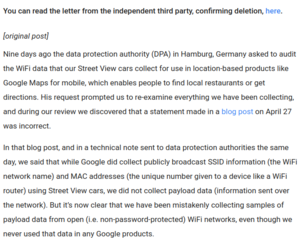
A screenshot of Google's official response to WiFi data collection.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Shiheni & përhapeni infografikën tonë →
hhldo3tnt5solzj2bwfvh7xm4slk2forpjwjyemhcfrlob5gq75gioid.onion

The banner for the 2022 Year in Review blog series
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Ver & compartir nuestra infografía →
hhldo3tnt5solzj2bwfvh7xm4slk2forpjwjyemhcfrlob5gq75gioid.onion

Cat Astronaut Soars Through Cyberspace, Leaving a Glowing Rainbow Trail
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
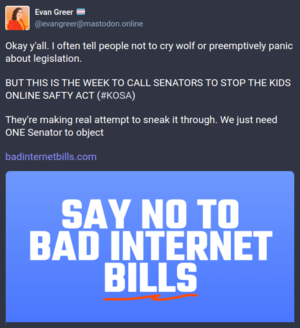
Screenshot of a Toot by Evan Greer saying it's time to stop KOSA.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
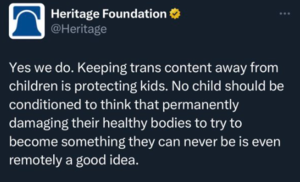
Screenshot of a Tweet by the Heritage Foundation.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Black and white picture of Nick thinking and looking to the left side.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
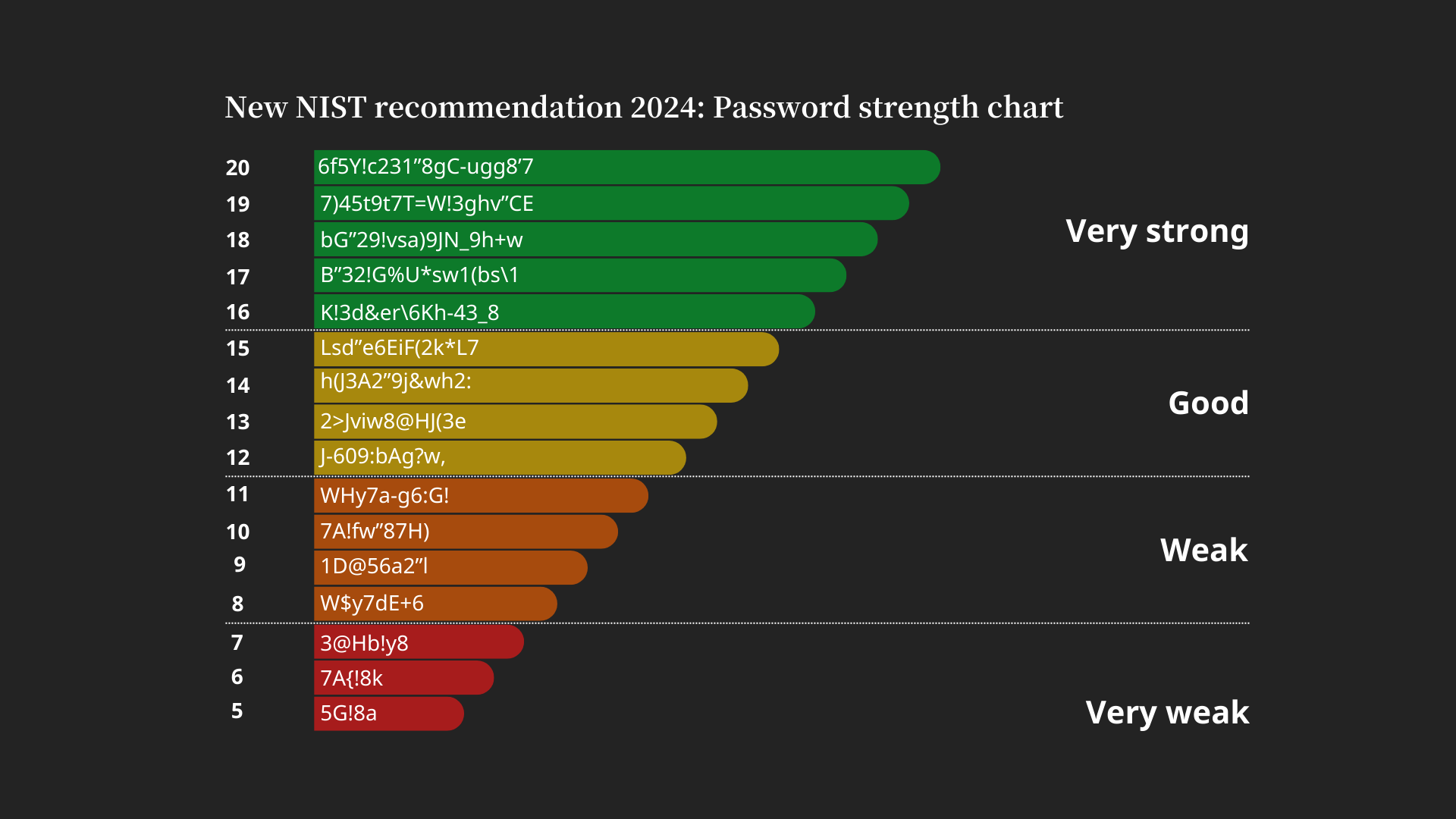
Chart on password security based on length and complexity according to 2024 recommendations by NIST and CISA
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
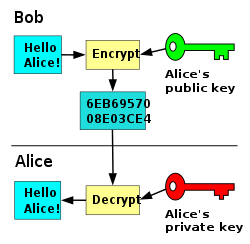
Eine visuelle Darstellung der asymmetrischen Verschlüsselung, die sowohl Daten verschlüsselt als auch entschlüsselt.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Das Versenden von sicheren Post-Quantum-E-Mails wird mit der in Tutanota integrierten Verschlüsselung zum Kinderspiel.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Military Model Enigma I, a cipher machine in use from 1930 to protect commercial, diplomatic, and military communication.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
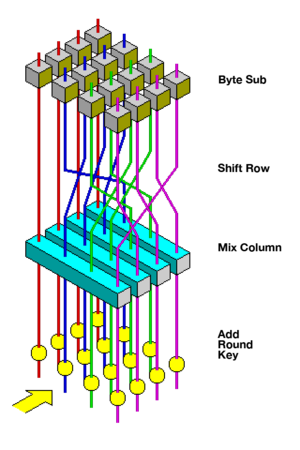
Ein Diagramm, das die Rundenfunktion von AES darstellt.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
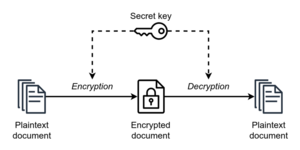
Ein einfaches Beispiel für die symmetrische Verschlüsselung.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Tuta Mail & Calendar features added in 2023
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

File:Lower Manhattan from Governors Island August 2017 panorama.jpg
7lvwsn4fohcnaw5ije6j52aurmwaovqdzj4drfrj5aqget3nwwneshid.onion

Data retention in Germany has finally been declared illegal.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

Client-seitiges Scannen würde die Verschlüsselung schwächen. Dies wird zu einer echten Bedrohung für alle, die auf den Schutz der Privatsphäre angewiesen sind, wie Aktivisten und Whistleblower.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
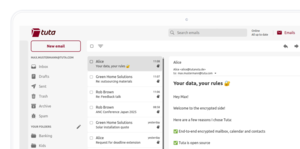
Laptop screen with the Tuta Mail app opened, displaying the inbox and an opened email, the subject line read
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Phone with the secure Tuta Mail app open displaying the email inbox. Enlarged in front of the phone is a note saying
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion