About 899 results found.
(Query 0.07500 seconds)
Ad
http://whm2fsi3ljgmhr7uxaepg2ywqgiinm4s52ln5nsbhis2w4jsfhkoawad.onion/product/2dyzbpKHeZCQNzx8EZvnAc8kd2RmVN6T
White House Market is a darknet marketplace that accepts Bitcoin (BTC) and Monero (XMR), and uses Multi-Sig wallets for users. WHM hosts more than 20,000 products spanning a wide range of categories, supported by several hundred verified vendors.
Ad
http://muwgjdckwwmhyi7lj73dspumrxmzuzjvujmtmyrhhbjrgswcakobtfad.onion
Handguns | Firearms | Buy Drugs | Cloned Cards| Paypal | Glocks For Sale | (EMAIL: [email protected])
Ad
http://deep6xcucd2o3ubqmuhwxiq37yw3fkroiwt74icyindute5znr2zpuad.onion
Telegram..@Darkdeep_admin to buy Cloned Cards, Gift Cards, Counterfeit Money, PayPal, Western Union, MoneyGram, Bank and Money Transfers, Guns & Ammunition, Drugs, Pills and research chemicals, Documents, certificates, diplomas, transcripts, hacking.
http://mubon4kdn4jx5xhj47ucfbcr3y3ajdfp5gjoazptrmfpwq7jmb632dyd.onion/stuff/disclaimers.html
This site contains copyrighted text stories only, there are no videos, photographs, drawings, or other visual images of any kind available on this site. Nialos Leaning 101 ways to say the same Read them all? and still here? Then you may continue to the stories .
http://zqktqfoeepjarikwyaw2j5f7rscyeb7bx62a2u2o2ajmxcl46c7xeiid.onion/index.php?title=The_Matrix&action=history
Everything the general public knows about the world, they know through the Matrix. The symbols and images the Matrix presents to them have become more real than reality itself . Hence the popularity of the ungodly abomination that is Reality TV.
1 similar result skipped
http://annualreport.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
Originally launched in 2014, EFF has continued to maintain and improve the tool, including the release of a new version that updates how we fight “link tracking” across several Google products including documents, email, maps, and images results. Privacy Badger now also removes tracking from links added after scrolling through Google Search results. Available to the public for free, Privacy Badger was the first add-on to specifically focus on blocking tracking in advertisements, instead of...
http://mf34jlghauz5pxjcmdymdqbe5pva4v24logeys446tdrgd5lpsrocmqd.onion/_modules/stem/descriptor/networkstatus.html
. * document header * list of :class:`stem.descriptor.networkstatus.DirectoryAuthority` * list of :class:`stem.descriptor.router_status_entry.RouterStatusEntry` * document footer **For a great graphical overview see** `Jordan Wright ' s chart describing the anatomy of the consensus < https://jordan-wright.github.io/images/blog/how_tor_works/consensus.png > `_. Of these, the router status entry section can be quite large (on the order of hundreds of kilobytes).
http://sy3tqe5tvukyk35kbqx4v3xjj5jxkrvrcdno4c4neg5kymz3zb5avzqd.onion/Bibles/English---Bible-in-Basic-English/Noted
This is the second death, even the sea of fire. ( Hadēs g86 , Limnē Pyr g3041 g4442 ) Revelation 20:15 And if anyone's name was not in the book of life, he went down into the sea of fire. ( Limnē Pyr g3041 g4442 ) Revelation 21:8 But those who are full of fear and without faith, the unclean and takers of life, those who do the sins of the flesh, and those who make use of evil powers or who give worship to images, and all those who are false, will have their part in the sea of ever-burning...
http://lechemintvwmunycley3gv2yef3fdfyr76wff4pcjvtqhhzacuwbylad.onion/archive/index.php?thread-113.html=
Il faut noter que la plupart des hébergeurs darknet sont souvent ciblés par les FDO. Deep Fake Vidéos ou images manipulées à l’aide d’IA (intelligence artificielle) pour imiter le visage ou la voix d’une personne réelle. Buts : désinformation et le chantage, usurpation d’identité, création de faux documents vidéo, ...
http://apcnasa3ozl2j74htizuzba5b6nhugbg2qze2nrz43siunkct555fpid.onion
No information is available for this page.
http://cardzoneqzvq6tkywkbpbbclp4sb4o4ry7piwkwx3om6qkxjmksb4zyd.onion/cz/wp-includes/js/dist/blocks.min.js
_){3,}[ \t]*$/gm,n),e=r.converter._dispatch("horizontalRule.after",e,t,r)})),a.subParser("images",(function(e,t,r){"use strict";function n(e,t,n,o,i,s,c,l){var u=r.gUrls,d=r.gTitles,p=r.gDimensions;if(n=n.toLowerCase(),l||(l=""),e.search(/\( ?
http://j5kv55yiu3rneydqn4f35kyhejbq3fhkkm7glg5nbtvxgaxthou7g2ad.onion/case-study.html
It can be
as simple as clicking a link and loading a URL, or even loading
images in your email client [30]: “As described in the proof-of-concept attack released by the
researchers, the attacker uses one of the encrypted messages you
are supposed to receive or might have already received and then
turns it into a multipart HTML email message, as well as forges
the return address, so it appears to come from...
http://pcards6wupxfbckwtmfzbd3mftzhiubblsesvdvi4l5q7euszihxudid.onion/index.html
If you have no idea what design or name to choose, we can make that choice for you or we can leave it blank if that's what you want. Click on the images below to see some examples of designs we can print. If none of those examples suit you, e-mail us a picture of the design you wish and we will make it happen.
2 similar results skipped
http://secure45nbquibuw6thmenrfamhobdkkrllgxrtayn4sgmnexremexyd.onion/guides/linux-hardening.html
To blacklist all wireless devices, execute: rfkill block all WiFi can be unblocked with: rfkill unblock wifi On systems using systemd, rfkill persists across sessions however, on systems using a
different init system, you may have to create an init script to execute these commands upon boot. 2.6 Other kernel pointer leaks Previous sections have prevented some kernel pointer leaks, but there are still a few more . On the filesystem, there exists the kernel images and System.map files...
http://ashicodepbnpvslzsl2bz7l2pwrjvajgumgac423pp3y2deprbnzz7id.onion/Ashigaru/Ashigaru-Terminal/commit/0bbed17ea5130bcf2aec5af6d3cc93f54aa9d871
Release binaries are also available directly from [ GitHub ]( https://github.com/sparrowwallet/sparrow/releases ). ___ 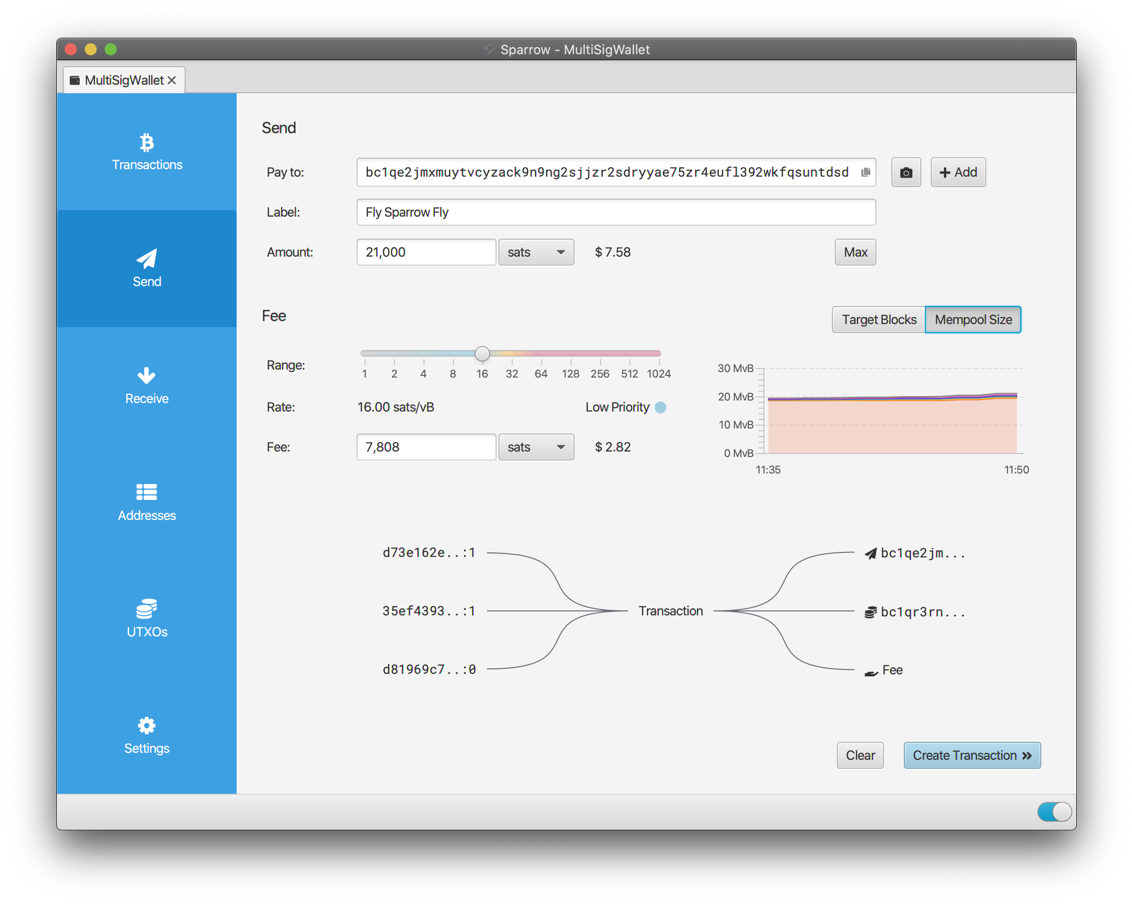 ### Software license: ## Building Ashigaru Terminal is released under the Free and Open Source license [ GNU GPLv3 ]( LICENSE ).
http://b4hntuy3fimfh2227vf4f74emnya7p35i5brtqujs6leqvtclfwvjbqd.onion/doc/physics/diamonds-crookes/The%20Project%20Gutenberg%20eBook%20of%20Diamonds,%20by%20William%20Crookes..html
Title : Diamonds Author : William Crookes Release date : January 4, 2020 [eBook #61096] Most recently updated: October 17, 2024 Language : English Credits : Produced by deaurider, John Campbell and the Online Distributed Proofreading Team at http://www.pgdp.net (This file was produced from images generously made available by The Internet Archive) *** START OF THE PROJECT GUTENBERG EBOOK DIAMONDS *** TRANSCRIBER’S NOTE Footnote anchors are denoted by [number] , and the footnotes have...
http://libraryqxxiqakubqv3dc2bend2koqsndbwox2johfywcatxie26bsad.onion/library/movement-for-no-society-movement-for-no-society
No information is available for this page.
http://meusartisdtyk3kjdt342w37z7m257ng76mtw5ycp5zrhjcfo2u2fkqd.onion/SPACE.html
No information is available for this page.




