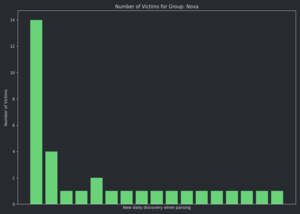
About 27,187 results found.
(Query 0.00700 seconds)
- All
- Images
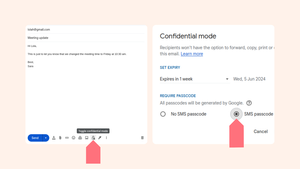
So senden Sie eine E-Mail mit dem vertraulichen Modus von Gmail.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion

So öffnen Sie eine passwortgeschützte E-Mail, die von Tuta Mail gesendet wurde: Klicken Sie auf den Link und geben Sie das Passwort ein.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
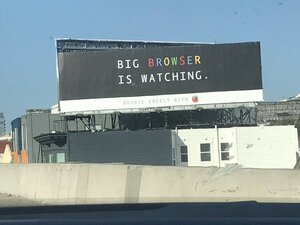
Mozilla anti-Google billboard advertisement
us63bgjkxwpyrpvsqom6kw3jcy2yujbplkhtzt64yykt42ne2ms7p4yd.onion

HIRE A HACKER TO SPY ON IPHONE WITH JUST THE NUMBER
7qfddt4adh36l3tfuircyan4gzp7vgwed6zi647v6vlfknwnhmewktyd.onion