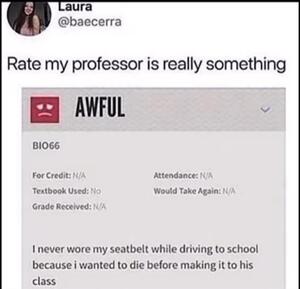
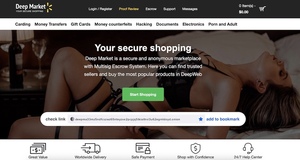
About 32,534 results found.
(Query 0.01400 seconds)
- All
- Images

Marshmallows roasting over the flames of a laptop in a forest with text: EFF Presents The Encryptids
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

Penguin flippers using pliers to put keys back on a broken laptop.
www.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion

BusKill: A USB Kill Cord for you Laptop
www.buskillvampfih2iucxhit3qp36i2zzql3u6pmkeafvlxs3tlmot5yad.onion

Hashish 15g DRY HASH [GOLD DRY GELATO]
domark3ru3jytfimrs2hahwmlj7lyhvffxiehrx6x5dne4x3yalltcyd.onion

3D Printable BusKill Proof of Concept (2023.08)
www.buskillvampfih2iucxhit3qp36i2zzql3u6pmkeafvlxs3tlmot5yad.onion

HOW TO FIND A QUALITY USED ENGINE FOR SALE
jtrrpneuko4qre2z5lilvhiw3shwbrnwkrvuuxcbj7t5khl4imoemayd.onion

The Hunter - Anti drone gun for Sale | drone-jamming guns | DroneGun Tactical | military anti drone gun buy online | Black Market Sale Anti drone Guns
bmguns3cak7kl7ksin2vho2gstg7vfz2lhr5s5aiiyfhfrfeevbtquid.onion