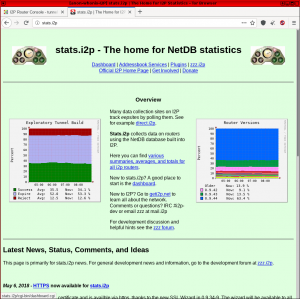
About 864 results found.
(Query 0.00700 seconds)
- All
- Images
Extract Shadowsocks client for Windows
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

Download Shadowsocks client for Windows from GitHub
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

II. Rechtsextremismus 1 Allgemeine Merkmale des Rechtsextremismus Der Rechtsextremismus verneint aus einer rassistischen und anti-liberalen Grundhaltung heraus die fundamentale Gleichheit aller Menschen. Die offene Staatsbürgergesellschaft ist ihm fremd.
zq5xve7vxljrsccptc4wxmuebnuiglhylahfwahyw7dzlxc43em4w6yd.onion

Unzipping the Xray core for Linux zip file
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

Xray core running in a Linux terminal
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion
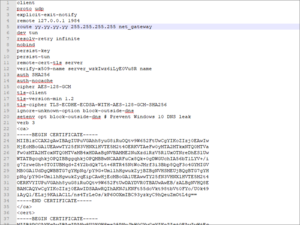
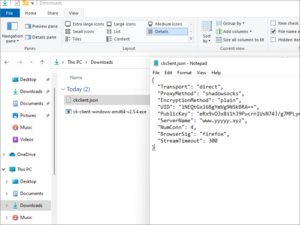
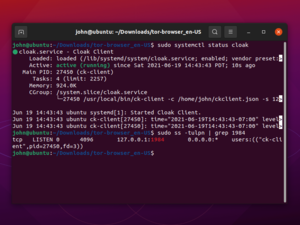
OpenVPN client configuration for Cloak
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

Tor Browser preferences for Tor settings
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

Displaying Tor circuit information in Tor Browser
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion

Tor Browser connecting to the Tor network
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion
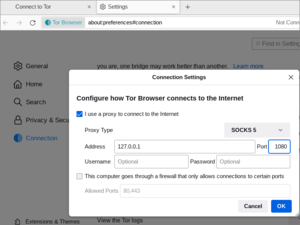
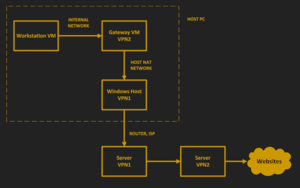
I use a proxy to connect to the Internet
gpp6nwvsps43b3mfacsh433uroo6uyjvvpr6tgj4jh4n5ngxt7rqbvid.onion