About 9,507 results found.
(Query 0.00500 seconds)
- All
- Images

The angular outline of three faces as a computer might see them, colored like a rainbow
kittens.iykpqm7jiradoeezzkhj7c4b33g4hbgfwelht2evxxeicbpjy44c7ead.onion
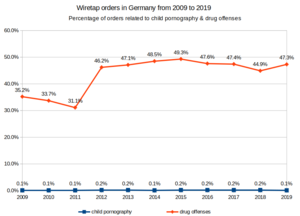
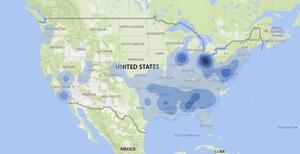
Comparison of the percentage of wiretap orders for child pornography and drug offenses in Germany, 2009-2019.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
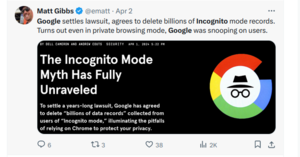
Google legt den Rechtsstreit um den Inkognito-Modus bei und erklärt sich bereit, Daten zu löschen.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion
Privacy win: Court rules that Google tricked people with Incognito Mode.
tutacomm6oqwlbbpd246mljjxpupuxxqj2jg5mfdyegeaetdauigslad.onion